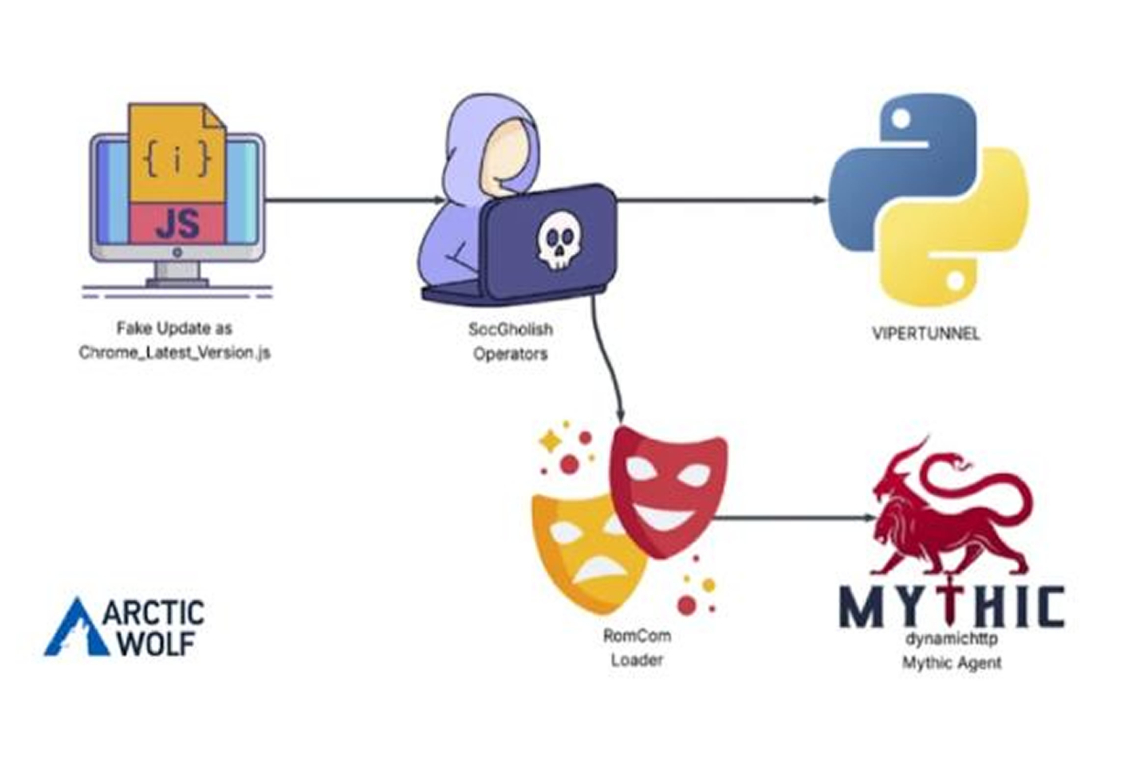
A threat actor using the RomCom malware family targeted a U.S. based civil engineering company by leveraging a malicious JavaScript loader known as SocGholish to ultimately deploy the Mythic Agent backdoor.
New Collaboration Between Threat Groups
This incident is notable because it marks the first time a RomCom payload has been observed being distributed by SocGholish (also known as FakeUpdates). RomCom is attributed with medium to high confidence to Unit 29155, a group linked to Russia’s GRU. The targeted
company had previously worked for a city with close ties to Ukraine, suggesting continued interest in entities connected to the region.
SocGholish, linked to the financially motivated operator TA569, typically functions as an initial access broker. It utilizes fake browser update alerts (for Chrome or Firefox) on compromised websites to trick users into downloading malicious JavaScript, which then fetches additional malware. The attacks primarily target poorly secured websites.
Infection and Espionage Tools
RomCom is a separate Russia aligned threat actor known for blending cybercrime and espionage operations since 2022. It uses various methods, including spear phishing and zero day exploits, to breach networks and drop its custom remote access trojan (RAT). Previous RomCom attacks have singled out entities in Ukraine and NATO related defense organizations.
In the attack analyzed by Arctic Wolf, the fake update payload allowed the threat actors to run commands on the compromised machine via a reverse shell to a command and control (C2) server.
The attack involved:
- Reconnaissance: Conducting initial checks on the compromised machine.
- Dropping VIPERTUNNEL: Installing a custom Python backdoor.
- Delivering Mythic Agent: Launching a RomCom linked DLL loader that delivered the Mythic Agent, a cross platform post exploit framework used for command execution and file operations.
The researchers observed that the timeline from initial infection via the fake update to the delivery of RomCom’s loader was less than 30 minutes. Delivery was not finalized until the target’s Active Directory domain was verified, highlighting the targeted nature of the campaign. Although the attack was ultimately blocked, it demonstrates RomCom’s continued interest in organizations providing support to Ukraine.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.