A Russia-linked threat group has been tied to a phishing campaign that exploits device code authentication workflows to steal Microsoft 365 credentials and execute account takeover attacks. The campaign, active since September 2025, is tracked by Proofpoint under the name UNK_AcademicFlare. Attackers have used compromised email accounts from government and military organizations to target entities in government, think tanks, higher education, and transportation sectors across the U.S. and Europe.
“Typically, these compromised accounts are leveraged for benign outreach and rapport-building related to the target’s area of expertise, ultimately leading to a fabricated meeting or interview,” Proofpoint explained.
As part of the scheme, victims receive a link to a document purportedly containing questions or topics for review before the meeting. The link directs users to a Cloudflare Worker page that mimics the sender’s Microsoft OneDrive account and instructs them to copy a code and click “Next” to access the document. This action redirects victims to Microsoft’s legitimate device code login page. When the provided code is entered, the service generates an access token, which attackers then retrieve to gain control of the victim’s account. Device code phishing was first detailed by Microsoft and Volexity in February 2025, with attribution to Russia-aligned clusters such as Storm-2372, APT29, UTA0304, and UTA0307. Recent reports from Amazon Threat Intelligence and Volexity warn of continued exploitation of this authentication flow by Russian threat actors.
Proofpoint assesses UNK_AcademicFlare as likely Russia-aligned, citing its focus on Russia specialists at think tanks and Ukrainian government and energy sector organizations. Data indicates that multiple actors—both state-sponsored and financially motivated—are adopting this phishing tactic to compromise Microsoft 365 accounts. One such e-crime group, TA2723, has used salary-themed lures to direct victims to fake landing pages and trigger device code authorization.
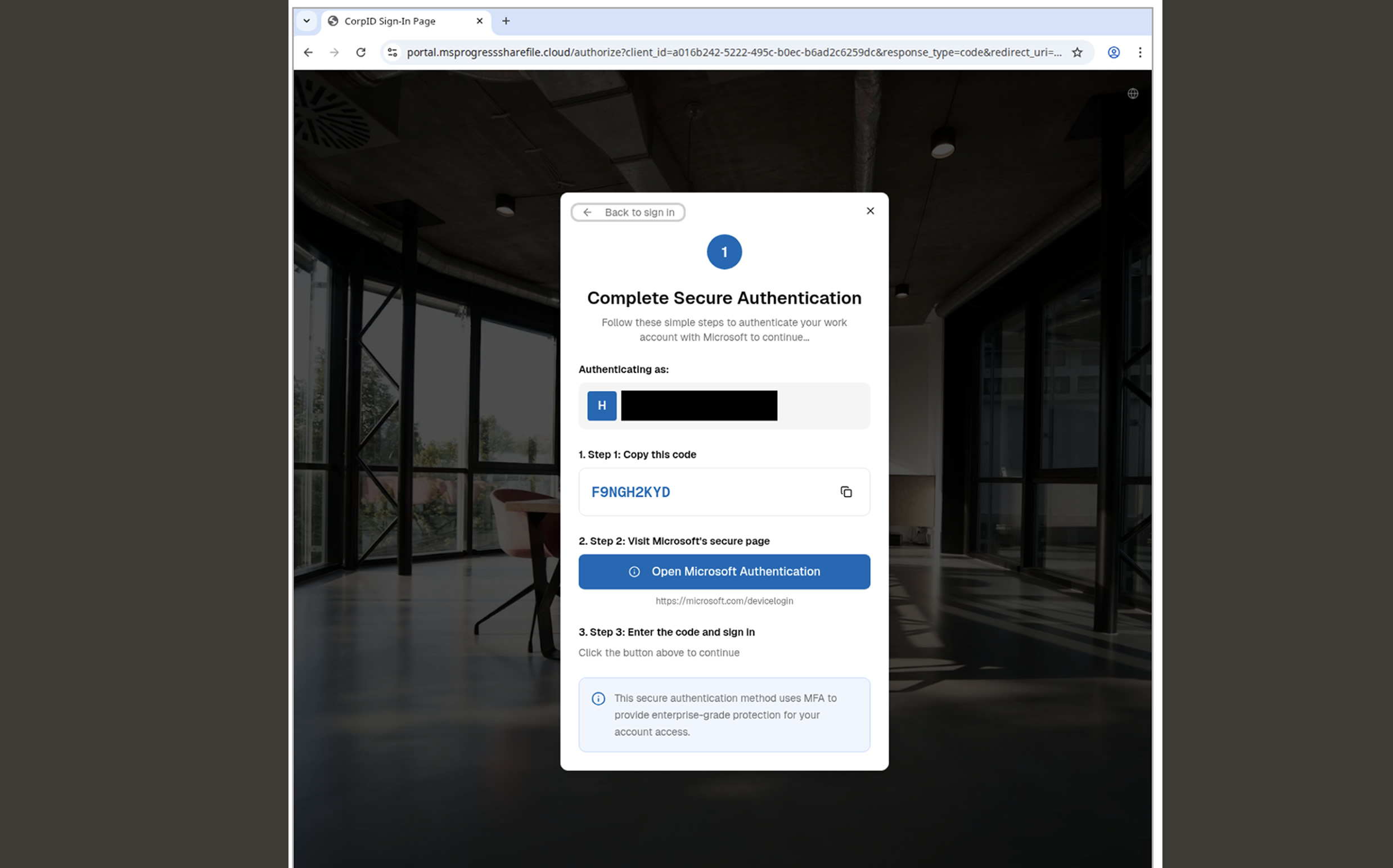
The October 2025 campaign appears to have been enabled by readily available crimeware tools like the Graphish phishing kit and red-team utilities such as SquarePhish. “Similar to SquarePhish, this tool is designed for ease of use and requires minimal technical expertise, lowering the barrier for entry and enabling even low-skilled actors to launch sophisticated phishing campaigns,” Proofpoint noted. The ultimate goal is unauthorized access to sensitive data for credential theft, account takeover, and further compromise.
To mitigate device code phishing risks, organizations should implement Conditional Access policies using the Authentication Flows condition to block device code flow for all users. If that’s not feasible, an allow-list approach should be adopted to permit device code authentication only for approved users, operating systems, or IP ranges.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.